"I spent 33 years and four months in active military service and during that period I spent most of my time as a high class muscle man for Big Business, for Wall Street and the bankers. In short, I was a racketeer, a gangster for capitalism. ... I helped in the raping of half a dozen Central American republics for the benefit of Wall Street. ... In China in 1927 I helped see to it that Standard Oil went on its way unmolested. Looking back on it, I might have given Al Capone a few hints. The best he could do was to operate his racket in three districts. I operated on three continents." Smedley Butler, Major General, U.S. Marine Corps.
Smedley Butler inspired my novel The Black Vault:
In the 1930s a group of wealthy industrialists plotted to overthrow President Franklin D. Roosevelt and replace him with a puppet dictator. The coup failed because of moral reservations of a single man: Smedley Butler.
Showing posts with label Espionage. Show all posts
Showing posts with label Espionage. Show all posts
01/03/2013
15/01/2013
Sock Puppet Social Media Friends
"The US military is developing software that will let it secretly manipulate social media sites by using fake online personas to influence internet conversations and spread pro-American propaganda."
Propaganda program "will allow one US serviceman or woman to control up to 10 separate identities based all over the world."
The military "stipulates that each fake online persona must have a convincing background, history and supporting details, and that up to 50 US-based controllers should be able to operate false identities from their workstations "without fear of being discovered by sophisticated adversaries"."
More: http://m.guardian.co.uk/technology/2011/mar/17/us-spy-operation-social-networks
SpyWriter Jack King "A new King of thrillers on the horizon" www.SpyWriter.com
Propaganda program "will allow one US serviceman or woman to control up to 10 separate identities based all over the world."
The military "stipulates that each fake online persona must have a convincing background, history and supporting details, and that up to 50 US-based controllers should be able to operate false identities from their workstations "without fear of being discovered by sophisticated adversaries"."
More: http://m.guardian.co.uk/technology/2011/mar/17/us-spy-operation-social-networks
SpyWriter Jack King "A new King of thrillers on the horizon" www.SpyWriter.com
14/01/2013
Unbreakable Codes

The Voynich Manuscript (1400-1500s)
Few encrypted texts are as mysterious – or as tantalizing – as the Voynich manuscript, a book dating to either 15th- or 16th-century Italy and written in a language no one understands, about a subject that no one can figure out, and involving illustrations of plants that don't exist. Plus it's got Zodiac symbols, astrological charts, illustrations of medicinal herbs, and drawings of naked womenbathing while hooked up to tubes.
The manuscript's 246 calfskin pages were perhaps meant for alchemy or medieval medicine, but no one knows for sure. What we do know is that it's written in a language distinct from any European language, and follows a pattern unique to its own. The alphabet ranges from 19 to 28 letters, with an average word length consistent with Greek- or Latin-derived languages, but is missing two-letter words while repeating words at a much higher rate than other European languages. All told, the book has 170,000 characters in it, written from left to right, and there are no punctuation marks.
William Friedman, one of the 20th century's greatest cryptographers, couldn't figure it out and suspected Voynich was a constructed, artificial language. (With no Rosetta Stone to help translate.) German computer scientist Klaus Schmeh suspected a hoax, and also suggested the manuscript's original language could have been encoded in a much larger set of "meaningless filler text." But there's no system for separating out the real text from the junk. Linguist and computer scientist Gordon Rugg also concluded the manuscript was a hoax.
Knight has been wrestling with Voynich for the better part of a decade, on and off. Recently, he and University of Chicago computer scientist Sravana Reddy discovered that the word length and frequency and the seeming presence of morphology – or the structure of word forms – "and most notably, the presence of page-level topics conform to natural language-like text."
The problem is that no one seems to know where to go next."
More unbreakable codes: http://www.wired.com/dangerroom/2012/12/codes/
SpyWriter Jack King "A new King of thrillers on the horizon" www.SpyWriter.com
13/12/2012
How technology shapes espionage
“So, we’re constantly looking and trying to figure out who are the intelligence officers and who are they meeting with? So, covert communications is the way that a spy passes information secretly to the handler, or the handler passes requests and other information back to the spy. ...
The way information is stored now makes it not only easier to use, but makes it far more vulnerable. If we can penetrate a network, we have everything. We own the kingdom.
So now, where throughout history spies stole the information and technology was used to convey it, it’s now just flipped around. The spy is now often the person that is simply the conveyor of the gadget that penetrates the network, because we now select spies, not by access to the secrets that they personally can get, but the access to the networks. So the person that maintains the network or the person that hypothetically buys the office equipment, such as the printers, could embed a chip into the printer and the printer, when they plug it into the network, now infects the entire network and now you’ve got a virus in the entire network. Now the human is the carrier of technology, as opposed to the technology being the carrier of small bits of information. How information is stores determines how vulnerable it is.”“The digital world has changed everything we know about espionage."
From: http://m.technobuffalo.com/2012/11/26/interview-spy-historian-h-k-melton-explains-how-tech-changed-spying-forever/
SpyWriter Jack King "A new King of thrillers on the horizon" www.SpyWriter.com
The way information is stored now makes it not only easier to use, but makes it far more vulnerable. If we can penetrate a network, we have everything. We own the kingdom.
So now, where throughout history spies stole the information and technology was used to convey it, it’s now just flipped around. The spy is now often the person that is simply the conveyor of the gadget that penetrates the network, because we now select spies, not by access to the secrets that they personally can get, but the access to the networks. So the person that maintains the network or the person that hypothetically buys the office equipment, such as the printers, could embed a chip into the printer and the printer, when they plug it into the network, now infects the entire network and now you’ve got a virus in the entire network. Now the human is the carrier of technology, as opposed to the technology being the carrier of small bits of information. How information is stores determines how vulnerable it is.”“The digital world has changed everything we know about espionage."
From: http://m.technobuffalo.com/2012/11/26/interview-spy-historian-h-k-melton-explains-how-tech-changed-spying-forever/
SpyWriter Jack King "A new King of thrillers on the horizon" www.SpyWriter.com
30/11/2012
The battle for your thoughts
"We have this position where as we know knowledge is power, and there’s a mass transfer as a result of literally billions of interceptions per day going from everyone, the average person, into the data vaults of state spying agencies for the big countries, and their cronies – the corporations that help build them that infrastructure. ...
The people who control the interception of the internet and, to some degree also, physically control the big data warehouses and the international fiber-optic lines. We all think of the internet as some kind of Platonic Realm where we can throw out ideas and communications and web pages and books and they exist somewhere out there. Actually, they exist on web servers in New York or Nairobi or Beijing, and information comes to us through satellite connections or through fiber-optic cables.
So whoever physically controls this controls the realm of our ideas and communications. And whoever is able to sit on those communications channels, can intercept entire nations, and that’s the new game in town, as far as state spying is concerned – intercepting entire nations, not individuals."
More: http://rt.com/news/assange-internet-control-totalitarian-943/
SpyWriter Jack King "A new King of thrillers on the horizon" www.SpyWriter.com
The people who control the interception of the internet and, to some degree also, physically control the big data warehouses and the international fiber-optic lines. We all think of the internet as some kind of Platonic Realm where we can throw out ideas and communications and web pages and books and they exist somewhere out there. Actually, they exist on web servers in New York or Nairobi or Beijing, and information comes to us through satellite connections or through fiber-optic cables.
So whoever physically controls this controls the realm of our ideas and communications. And whoever is able to sit on those communications channels, can intercept entire nations, and that’s the new game in town, as far as state spying is concerned – intercepting entire nations, not individuals."
More: http://rt.com/news/assange-internet-control-totalitarian-943/
SpyWriter Jack King "A new King of thrillers on the horizon" www.SpyWriter.com
25/11/2012
Spying, it's a women's world

"On a moonlit night in June 1943, Noor, fresh from spy school at Beaulieu, was the first female radio operator ever to be dropped into Nazi-occupied France. As part of a network of agents responsible for sending intelligence back to England, “Madeleine” was equipped with a transmitter/receiver device, weighing about 30 pounds and fitting into an ordinary suitcase. With German wireless direction-finding vehicles — typically disguised as laundry and baker’s vans — regularly circling round, she had to be constantly vigilant, always finding surreptitious new locations and never staying on air for long. It was also crucial that she gave the unwavering impression of being completely French, never uttering a word or displaying a gesture that might give her away. For emergencies, she had four pills: Benzedrine, in case she needed to stay awake for a long spell; a sleeping pill, to drop in an enemy’s drink in a tight spot; a drug to induce stomach disturbance; and of course cyanide, to be bitten if she chose to die rather than endure torture or interrogation."
More: http://www.salon.com/2012/11/08/the_spy_game_no_men_need_apply/?mobile.html
Jack King "A new King of thrillers": www.SpyWriter.com
24/11/2012
Espionage and Surveillance State in the Elizabethan Age
"We think of the surveillance state as a modern development, something conjured up by novels such as Joseph Conrad's The Secret Agent or George Orwell's 1984, or by real-life stories of Stalin's Soviet Union or Hitler's Germany. But spying is one of the world's oldest professions, as the Iliad, the Odyssey, and the Bible attest. Well before the 20th century, many states were doing all they could to monitor their citizens' activities as closely and comprehensively as possible.
England in particular has a long history of spying on its own people. It is no accident that in Hamlet, Shakespeare portrays the Danish government specializing in espionage and double-dealing. In Act 2, scene 1, the court councilor Polonius teaches a henchman how to spy on Polonius' own son, Laertes, in Paris, instructing him "by indirections find directions out." Moving as he did in court circles, Shakespeare was evidently familiar with intelligence operations in Elizabethan England, some of which involved several of his famous contemporaries—certainly Francis Bacon and possibly Christopher Marlowe. Under such spymasters as Lord Burghley and Francis Walsingham, Queen Elizabeth's court pioneered many of the techniques and practices we associate with international espionage to this day, including code-breaking and the use of double and even triple agents."
More: http://reason.com/archives/2012/11/24/the-elizabethan-cia
Jack King "A new King of thrillers": www.SpyWriter.com
England in particular has a long history of spying on its own people. It is no accident that in Hamlet, Shakespeare portrays the Danish government specializing in espionage and double-dealing. In Act 2, scene 1, the court councilor Polonius teaches a henchman how to spy on Polonius' own son, Laertes, in Paris, instructing him "by indirections find directions out." Moving as he did in court circles, Shakespeare was evidently familiar with intelligence operations in Elizabethan England, some of which involved several of his famous contemporaries—certainly Francis Bacon and possibly Christopher Marlowe. Under such spymasters as Lord Burghley and Francis Walsingham, Queen Elizabeth's court pioneered many of the techniques and practices we associate with international espionage to this day, including code-breaking and the use of double and even triple agents."
More: http://reason.com/archives/2012/11/24/the-elizabethan-cia
Jack King "A new King of thrillers": www.SpyWriter.com
09/11/2012
The end of espionage thriller?
Can't find a decent espionage thriller these days? Don't blame it on Perestroika. Blame it on not reading SpyWriter Jack King:
"The end of the Cold War created a problem for espionage thriller writers and moviemakers. They faced loss of a built-in backstory needing no explanation, a whole set of strong but realistic motivations for extreme behavior, a pre-fab cast of bad guys, and weighty, global stakes underlying all the action. Perestroika left a generation of writers searching for new conflicts and settings and plot devices.
Today I think the growth of surveillance technology will increasingly create a similar problem for fiction writers. It’s a staple of thrillers and science fiction to have the hero on the run—hounded by the government, evading the police—either because the hero is mistaken as someone bad or because the government is evil. And the government baddies use every technology at their disposal to locate and track their target, while the hero uses tricks and hacks to escape detection.
But the whole cat and mouse game is starting to look kind of problematic, because it’s getting harder to sustain a plausible “man on the run” scenario in the face of surveillance technology.
I like a good airport thriller or science fiction read, and for several years I’ve noticed this problem cropping up: it’s the near future (or later), the hero or heroine is on the run, and I find myself thinking, oh please, if they really had all the advanced technologies featured in this story, they’d certainly have more impressive surveillance capability! We may have more than that ourselves in couple years the way things are going."
From: http://www.aclu.org/blog/technology-and-liberty-national-security/will-increasing-surveillance-change-fiction
Presidents are chosen, but not elected. The Black Vault. www.SPYWRITER.com
"The end of the Cold War created a problem for espionage thriller writers and moviemakers. They faced loss of a built-in backstory needing no explanation, a whole set of strong but realistic motivations for extreme behavior, a pre-fab cast of bad guys, and weighty, global stakes underlying all the action. Perestroika left a generation of writers searching for new conflicts and settings and plot devices.
Today I think the growth of surveillance technology will increasingly create a similar problem for fiction writers. It’s a staple of thrillers and science fiction to have the hero on the run—hounded by the government, evading the police—either because the hero is mistaken as someone bad or because the government is evil. And the government baddies use every technology at their disposal to locate and track their target, while the hero uses tricks and hacks to escape detection.
But the whole cat and mouse game is starting to look kind of problematic, because it’s getting harder to sustain a plausible “man on the run” scenario in the face of surveillance technology.
I like a good airport thriller or science fiction read, and for several years I’ve noticed this problem cropping up: it’s the near future (or later), the hero or heroine is on the run, and I find myself thinking, oh please, if they really had all the advanced technologies featured in this story, they’d certainly have more impressive surveillance capability! We may have more than that ourselves in couple years the way things are going."
From: http://www.aclu.org/blog/technology-and-liberty-national-security/will-increasing-surveillance-change-fiction
Presidents are chosen, but not elected. The Black Vault. www.SPYWRITER.com
29/10/2012
The subtle difference between a "spy" and an "intelligence agent"
Q: "What exactly were you doing in the U.S.? What is it called? Spying?"
A: "It’s the same thing the American special services are doing in Russia. The English word “spy” may refer to what the Russians call “spy” or “intelligence agent.” It depends on how you look at it. It’s no accident that, in the Soviet Union, the good guys were called “intelligence agents” and the enemies were called “spies.” ...
"intelligence does not work against specific people. It’s not permanent and assignments can change. As a secret agent, you work for the good of your country. Crimes may be committed against specific people, but intelligence is a patriotic business."
More: http://indrus.in/articles/2012/10/19/russian_spy_reveals_his_secrets_18485.html
A: "It’s the same thing the American special services are doing in Russia. The English word “spy” may refer to what the Russians call “spy” or “intelligence agent.” It depends on how you look at it. It’s no accident that, in the Soviet Union, the good guys were called “intelligence agents” and the enemies were called “spies.” ...
"intelligence does not work against specific people. It’s not permanent and assignments can change. As a secret agent, you work for the good of your country. Crimes may be committed against specific people, but intelligence is a patriotic business."
More: http://indrus.in/articles/2012/10/19/russian_spy_reveals_his_secrets_18485.html
Miniature spying insects
A miniature spying insect:

"Next time a pesky insect lands on you take a close look at it before you swat it away because you could be in for a nasty surprise.
What might appear to be a mosquito or something similar could, in fact, be a miniature spy drone which is snooping on you and being controlled by someone thousands of kilometres away."
More: http://www.nbr.co.nz/article/beware-intelligent-insects-they-are-spying-you-weekend-review-rv-131241

What might appear to be a mosquito or something similar could, in fact, be a miniature spy drone which is snooping on you and being controlled by someone thousands of kilometres away."
More: http://www.nbr.co.nz/article/beware-intelligent-insects-they-are-spying-you-weekend-review-rv-131241
18/10/2012
The Shop
"The CIA is not in the habit of discussing its clandestine operations, but the agency’s purpose is clear enough. As then-chief James Woolsey said in a 1994 speech to former intelligence operatives: “What we really exist for is stealing secrets.” [...]
That is why by 1955, and probably earlier, the CIA created a special unit to perform what the agency calls “surreptitious entries.” This unit was so secret that few people inside CIA headquarters knew it existed; it wasn’t even listed in the CIA's classified telephone book. Officially it was named the Special Operations Division, but the handful of agency officers selected for it called it the Shop.
[...] in the 1980s and early ’90s, the Shop occupied a nondescript one-story building just south of a shopping mall in the Washington suburb of Springfield, Virginia. The building was part of a government complex surrounded by a chain-link fence; the pebbled glass in the windows let in light but allowed no view in or out. The men and women of the Shop made up a team of specialists: lock pickers, safecrackers, photographers, electronics wizards and code experts. One team member was a master at disabling alarm systems, another at flaps and seals. Their mission, put simply, was to travel the world and break into other countries’ embassies to steal codes"
More: http://www.smithsonianmag.com/history-archaeology/The-CIA-Burglar-Who-Went-Rogue-169800816.html?c=y&page=2
Jack King's new novel: The Black Vault
That is why by 1955, and probably earlier, the CIA created a special unit to perform what the agency calls “surreptitious entries.” This unit was so secret that few people inside CIA headquarters knew it existed; it wasn’t even listed in the CIA's classified telephone book. Officially it was named the Special Operations Division, but the handful of agency officers selected for it called it the Shop.
[...] in the 1980s and early ’90s, the Shop occupied a nondescript one-story building just south of a shopping mall in the Washington suburb of Springfield, Virginia. The building was part of a government complex surrounded by a chain-link fence; the pebbled glass in the windows let in light but allowed no view in or out. The men and women of the Shop made up a team of specialists: lock pickers, safecrackers, photographers, electronics wizards and code experts. One team member was a master at disabling alarm systems, another at flaps and seals. Their mission, put simply, was to travel the world and break into other countries’ embassies to steal codes"
More: http://www.smithsonianmag.com/history-archaeology/The-CIA-Burglar-Who-Went-Rogue-169800816.html?c=y&page=2
Jack King's new novel: The Black Vault
09/10/2012
IFOs - Identified Flying Objects
UFOs become IFOs. Those flying saucers you thought you saw did exist, after all. Schematics declassified:
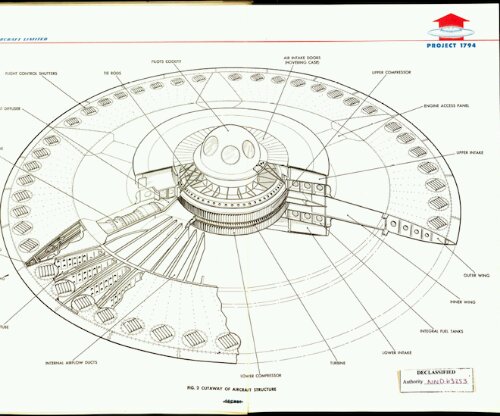
More: http://www.wired.com/dangerroom/2012/10/the-airforce/
The Election. The Coup. The Black Vault. www.SPYWRITER.com

More: http://www.wired.com/dangerroom/2012/10/the-airforce/
The Election. The Coup. The Black Vault. www.SPYWRITER.com
03/10/2012
How To Beat a Lie Detector
You don't have be employed in the security sector to be subjected to a polygraph test. Sooner or later, on a variety of reasons, you may face one. It doesn't have to be a stressful experience, it won't be if you take the time to prepare. It may even turn out to be quite fun. Purchase a set (available directly from China) that plugs into your laptop, invite some friends, and play a round of truth or lies...
"First, Tice says, a person can trick the tester on "probable-lie" questions. During a polygraph's pre-test interview, the tester usually asks a person to answer questions they are likely to lie about.
These include questions like: 'Have you ever stolen money?,' 'Have you ever lied to your parents?,' or 'Have you ever cheated on a test?'.
Most people have done these at least once, but lie about it. So the tester uses a person's response to a likely lie as a way to establish how a person physically reacts while lying.
Tice says to trick the tester, a person should lie in response to these questions like most other people would, but also bite their tongue hard while doing so, which will set off other physiological reactions in the body.
The tester's "needles will fly everywhere," says Tice, "and he will think, 'This guy is a nervous nelly. He has a strong physical reaction when he's lying.'"
"And you're skewing the test," he says. Tice says it's also easy to beat a polygraph while telling a real lie by daydreaming to calm the nerves."
More: http://www.usnews.com/news/blogs/washington-whispers/2012/09/25/nsa-whistleblower-reveals-how-to-beat-a-polygraph-test
WikiJustice: WikiLeaks meets Jack London's The Assassination Bureau, Ltd. www.SPYWRITER.com
"First, Tice says, a person can trick the tester on "probable-lie" questions. During a polygraph's pre-test interview, the tester usually asks a person to answer questions they are likely to lie about.
These include questions like: 'Have you ever stolen money?,' 'Have you ever lied to your parents?,' or 'Have you ever cheated on a test?'.
Most people have done these at least once, but lie about it. So the tester uses a person's response to a likely lie as a way to establish how a person physically reacts while lying.
Tice says to trick the tester, a person should lie in response to these questions like most other people would, but also bite their tongue hard while doing so, which will set off other physiological reactions in the body.
The tester's "needles will fly everywhere," says Tice, "and he will think, 'This guy is a nervous nelly. He has a strong physical reaction when he's lying.'"
"And you're skewing the test," he says. Tice says it's also easy to beat a polygraph while telling a real lie by daydreaming to calm the nerves."
More: http://www.usnews.com/news/blogs/washington-whispers/2012/09/25/nsa-whistleblower-reveals-how-to-beat-a-polygraph-test
WikiJustice: WikiLeaks meets Jack London's The Assassination Bureau, Ltd. www.SPYWRITER.com
27/09/2012
Dissolvable espionage
Imagine spy devices that dissolve completely into nothingness...
"The technology, which will be announced in a paper this week in Science, is called transient electronics or resorbable electronics. These systems work until they are no longer needed, at which point they dissolve completely away—the dissolution triggered by ordinary water in their operating environment. ...
It's not hard to imagine the uses of small electronic devices that vanish without a trace when exposed to water. Disappearing sensors and other spy gear could be air-dropped or strategically embedded in hostile environments with no one the wiser. ...
The work is being funded in part by DARPA, the Defense Department's mad science arm, which sees a range of applications. To no one's surprise, though, those uses are classified."I can't get into those details," he tells PM." Source: http://www.popularmechanics.com/science/health/breakthroughs/transient-electronics-could-dissolve-inside-your-body-13098637?click=pm_latest
The spies can't tell you what their plans are, but this thriller writer can - a spy device based on the above concept is used by characters in my latest novel THE BLACK VAULT: http://www.spywriter.com/tbv/index.html
END OF POST
"The technology, which will be announced in a paper this week in Science, is called transient electronics or resorbable electronics. These systems work until they are no longer needed, at which point they dissolve completely away—the dissolution triggered by ordinary water in their operating environment. ...
It's not hard to imagine the uses of small electronic devices that vanish without a trace when exposed to water. Disappearing sensors and other spy gear could be air-dropped or strategically embedded in hostile environments with no one the wiser. ...
The work is being funded in part by DARPA, the Defense Department's mad science arm, which sees a range of applications. To no one's surprise, though, those uses are classified."I can't get into those details," he tells PM." Source: http://www.popularmechanics.com/science/health/breakthroughs/transient-electronics-could-dissolve-inside-your-body-13098637?click=pm_latest
The spies can't tell you what their plans are, but this thriller writer can - a spy device based on the above concept is used by characters in my latest novel THE BLACK VAULT: http://www.spywriter.com/tbv/index.html
END OF POST
24/08/2012
Espionage Monopoly

More: http://www.mnn.com/green-tech/gadgets-electronics/stories/4-unbelievable-spy-gadgets
###END OF POST###
THE BLACK VAULT by Jack King:
It's the year of
07/08/2012
Know your online friends
How well do you know your Social Networking "Friends"?
"the U.S. Strategic Command (overseeing the nuclear strike) will concentrate on military computer hacking and cyberdefenses. The Joint Staffs will take responsibility for deception operations, while Special Operations Command will take the lead in military information gathering aimed at supporting secret operations. [...] the Central Command (covering the greater Middle East) has recently purchased a $2.7 million software, especially designed by San-Diego based Ntrepid. The material will permit the manipulation of social media through the use of fake online "personas" managed by the military, followed by all kinds of infiltration and intelligence operations, while being able to keep the trickery under the radar."
http://www.voltairenet.org/article168698.html
### END OF POST ###
www.SPYWRITER.com
"the U.S. Strategic Command (overseeing the nuclear strike) will concentrate on military computer hacking and cyberdefenses. The Joint Staffs will take responsibility for deception operations, while Special Operations Command will take the lead in military information gathering aimed at supporting secret operations. [...] the Central Command (covering the greater Middle East) has recently purchased a $2.7 million software, especially designed by San-Diego based Ntrepid. The material will permit the manipulation of social media through the use of fake online "personas" managed by the military, followed by all kinds of infiltration and intelligence operations, while being able to keep the trickery under the radar."
http://www.voltairenet.org/article168698.html
### END OF POST ###
www.SPYWRITER.com
25/07/2012
Loneliness of a double life
As new school year approaches and recruiters will be sweeping every campus for impressionable youth it may be a good idea to recount what it is like to be a spy:
"Intelligence agents lead double lives, requiring them to regularly deceive other people, and not just their targets. It is not easy for a person with a solid social conscience to sustain a lifestyle that involves covertly influencing or controlling others through lies. Agents can come to feel subtly detached or separated from other people, feelings that may persist even when they resume their normal lives once their espionage is over.
These psychological burdens of detachment and loneliness are acute while the agents are deployed and living their covers among their targets, where the seemingly trusting social relationships they have built with targets are mostly false, based on lies and manipulation. Sometimes they frankly despise the targets they are pretending to admire. Their real personalities are buried under layers of clandestinity; there is no one there who is aware of their true status, other than themselves. One particularly self-aware agent described his psychological situation while deployed as a form of solitary confinement, with his own skull his prison cell."
More: http://www.brookings.edu/research/opinions/2012/07/05-spy-wilder
### END OF POST ###
www.SPYWRITER.com
"Intelligence agents lead double lives, requiring them to regularly deceive other people, and not just their targets. It is not easy for a person with a solid social conscience to sustain a lifestyle that involves covertly influencing or controlling others through lies. Agents can come to feel subtly detached or separated from other people, feelings that may persist even when they resume their normal lives once their espionage is over.
These psychological burdens of detachment and loneliness are acute while the agents are deployed and living their covers among their targets, where the seemingly trusting social relationships they have built with targets are mostly false, based on lies and manipulation. Sometimes they frankly despise the targets they are pretending to admire. Their real personalities are buried under layers of clandestinity; there is no one there who is aware of their true status, other than themselves. One particularly self-aware agent described his psychological situation while deployed as a form of solitary confinement, with his own skull his prison cell."
More: http://www.brookings.edu/research/opinions/2012/07/05-spy-wilder
### END OF POST ###
www.SPYWRITER.com
18/06/2012
The Black Vault
THE BLACK VAULT is any spy agency's most prized possession - those dirty and unaccountable funds that provide operational freedom outside of governmental scrutiny. They fund black operations - the stuff too dirty for any government to admit to.
How is the black vault funded, and what purpose does it serve?
"In the past, the CIA has been implicated in numerous scandals involving drug and weapons trafficking. From Vietnam and Iran to Latin America, the agency has repeatedly been caught importing narcotics and exporting arms for shadowy and subversive purposes."
"Citing an unnamed CIA source, a Washington Times article theorizes that U.S. officials were actively aiding organizations such as the Sinaloa cartel with guns and immunity in an effort to stymie Los Zetas. That’s because, according to the piece, the powerful and brutal criminal Zetas syndicate has the potential to overthrow the government of Mexico — and might be planning to do so."
Source: http://www.thenewamerican.com/world-mainmenu-26/north-america-mainmenu-36/8599-reports-cia-working-with-mexican-drug-cartels
What are black operations? What is the Black Vault? How is The Black Vault used? This, and more, in Jack King's new thriller novel: THE BLACK VAULT
[caption id="" align="aligncenter" width="500" caption="The black vault"] [/caption]
[/caption]
### END OF POST ###
www.SPYWRITER.com
How is the black vault funded, and what purpose does it serve?
"In the past, the CIA has been implicated in numerous scandals involving drug and weapons trafficking. From Vietnam and Iran to Latin America, the agency has repeatedly been caught importing narcotics and exporting arms for shadowy and subversive purposes."
"Citing an unnamed CIA source, a Washington Times article theorizes that U.S. officials were actively aiding organizations such as the Sinaloa cartel with guns and immunity in an effort to stymie Los Zetas. That’s because, according to the piece, the powerful and brutal criminal Zetas syndicate has the potential to overthrow the government of Mexico — and might be planning to do so."
Source: http://www.thenewamerican.com/world-mainmenu-26/north-america-mainmenu-36/8599-reports-cia-working-with-mexican-drug-cartels
What are black operations? What is the Black Vault? How is The Black Vault used? This, and more, in Jack King's new thriller novel: THE BLACK VAULT
[caption id="" align="aligncenter" width="500" caption="The black vault"]
 [/caption]
[/caption]### END OF POST ###
www.SPYWRITER.com
02/03/2012
Leftist beliefs cause cancer (with a little help from the CIA)

"The gun fired a frozen liquid poison-tipped dart, the width of a human
hair and a quarter of an inch long, that could penetrate clothing, was
almost undetectable and left no trace in a victim’s body."
"It was a case destined for the X-Files and conspiracy theorists alike, when Venezuelan president Hugo Chavez speculated that the US might have developed a way to weaponise cancer, after several Latin American leaders were diagnosed with the disease. The list includes former Argentine president, Nestor Kirchner (colon cancer) Brazil’s president Dilma Rousseff (lymphoma cancer), her predecessor Luiz Inacio Lula da Silva (throat cancer), Chavez (undisclosed), former Cuban president Fidel Castro (stomach cancer) Bolivian president, Evo Morales (nasal cancer) and Paraguayan president Fernando Lugo (lymphoma cancer). What do they have in common besides cancer? All of them are left-wing leaders. Coincidence? In his December 28, 2011 end-of-year address to the Venezuelan military, Chavez hinted that the US might have found a way to give Latin American leaders cancer.
“Would it be so strange that they’ve invented the technology to spread cancer and we won’t know about it for 50 years?” Chavez asked. “It is very hard to explain, even with the law of probabilities, what has been happening to some leaders in Latin America. It’s at the very least strange,” he said. Chavez said he received warning from Cuba’s former leader Fidel Castro, who has survived hundreds of unsuccessful assassination attempts. “Fidel always told me, ‘Chavez take care. These people have developed technology. You are very careless. Take care what you eat, what they give you to eat … a little needle and they inject you with I don’t know what’,” he said."
More: http://www.guardian.co.tt/lifestyle/2012-02-27/cancer-secret-weapon
###END OF POST###
www.SPYWRITER.com
27/02/2012
The Bridge of Spies
[caption id="" align="aligncenter" width="500" caption="The bridge od spies"] [/caption]
[/caption]
On June 12, 1985, Marian Zacharski, a Polish spy, was exchanged for 25 American agents.
"Polish-born, Marian Zacharski adopted the guise of a legitimate businessman in the United States in the late 1970s. The reportedly handsome and resourceful agent befriended William Holden Bell, an engineer at Hughes Aircraft. Over the course of three years, Zacharski persuaded Bell to pass along plans for secret radar systems and some of the technology behind early stealth aircraft. Zacharski’s tactics in recruiting Bell were so impressive that they are still studied by the FBI decades later."
More spy exchanges: http://www.history.com/news/2012/02/10/prisoner-exchanges-across-the-bridge-of-spies-from-powers-to-shcharansky/
### END OF POST ###
www.SPYWRITER.com
 [/caption]
[/caption]On June 12, 1985, Marian Zacharski, a Polish spy, was exchanged for 25 American agents.
"Polish-born, Marian Zacharski adopted the guise of a legitimate businessman in the United States in the late 1970s. The reportedly handsome and resourceful agent befriended William Holden Bell, an engineer at Hughes Aircraft. Over the course of three years, Zacharski persuaded Bell to pass along plans for secret radar systems and some of the technology behind early stealth aircraft. Zacharski’s tactics in recruiting Bell were so impressive that they are still studied by the FBI decades later."
More spy exchanges: http://www.history.com/news/2012/02/10/prisoner-exchanges-across-the-bridge-of-spies-from-powers-to-shcharansky/
### END OF POST ###
www.SPYWRITER.com
Subscribe to:
Posts (Atom)
